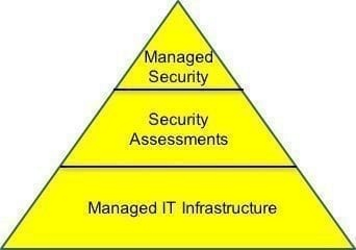
I’ve been thinking a lot about triangles lately. Not the musical kind, but rather how they are such a useful (and simple) means of conveying building blocks and foundations. Notably the Foundations of IT Security:

With this (very) basic illustration I’d like to convey the main message of this blog piece. Namely that it’s essential to have a professionally established and managed IT infrastructure in your business before you embark on cyber security assessments, hardening, plugging gaps and so forth. In other words, get your foundations of IT security in place.
Cyber security is all the rage presently but, let’s face it, the requirement will never go away as long as we have the internet. Regrettably there are talented IT people who direct their energies towards obtaining information about individuals and companies for their own financial gain. We can’t change that, we can do our best to protect ourselves against it.
So what strategies can be employed to counter the cyber threat? Well, the cyber services offered by CCS are aligned to provide all the necessary counter measures, including:
- Cyber Awareness Training
- Continuous Protective Monitoring
- Cyber Intelligence Assessment
- Cyber Assessment Services
- Cyber Essentials Scheme
- Cyber Security Support Packages
- ISO27001 compliance
All of these are outlined in detail on the CCS website. However, before embarking on any of these services, you should consider the following basic questions relating to your current IT infrastructure.
- Do you have a password policy and enforced password-change policy?
- Do you have a server? If so, do you insist that all staff store their data on the server, not their desktop PCs?
- What operating systems are you running on your server and PCs? Are they still supported? (Take a look at Microsoft out-of-support systems here)
- Do you know if you have conducted health-checks on your server and PCs in the last 6 months?
- Do you have backup solutions in place for your data?
- Do you have a paid antivirus solution in place? (Sorry – as with all things in life you get what you pay for. Free anti-virus does not provide anything close to sufficient protection)
- Do you have a Firewall in-place?
If you can’t honestly answer yes to these questions (and many others not touched upon here), then you need to obtain professional advice and management for your IT systems. Ignoring the security aspects for a moment, if you take care of the above matters your internal systems will run more efficiently. However, you really can’t ignore the security aspects. SMEs are just as likely to be targeted as big corporations.
So whether you’re a small, medium or huge business, professional IT system setup and management form the basis of your foundations of IT security. They’re a pre-requisite for cyber security.
Please, get it done, if for no other reason than you’ll sleep easier at night.